Add File Protect rules
The File Protect feature in Xprotect is an additional layer of security for hosts that have already been enforced with Application Control policies. File Protect can help you lock down applications to data and/or file access on the hosts.
In an Xprotect policy (applies to both Host policy and User policy), File Protect rules are processed before the Application Control rules. Also, unlike Application Control violations that can be monitored and allowed, File Protect violations are never allowed.
File Protect rules
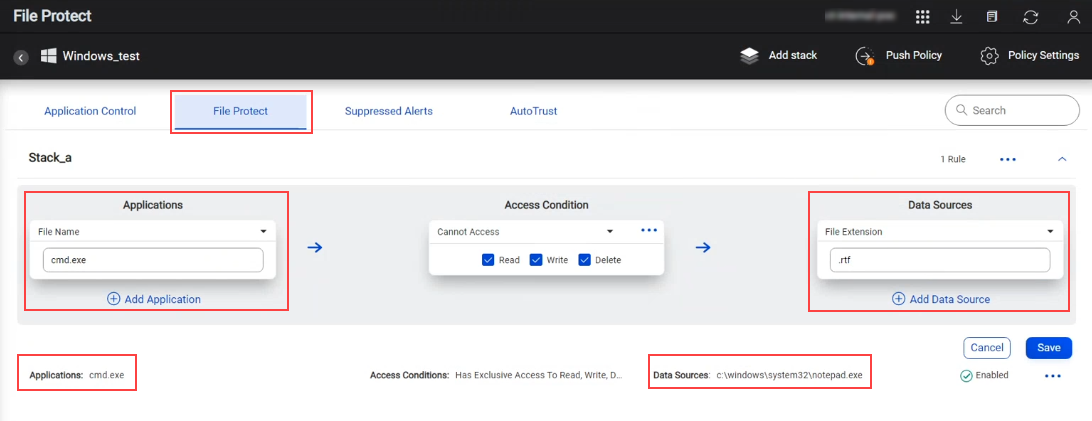
A File Protect rule is enforced between Applications (the accessors) and the Data sources (the protected entities such as files or other data) on a host. You can set specific levels of Scopes (files or folders on the hosts) for the Applications and Data Sources involved in the rule and define the nature of access (read, write, delete) through Access Conditions.
File Protect overwrites the existing permissions natively assigned (by the OS controller) to the related Applications and Data Sources on a host. After the File Protect rules are pushed and enforced on a host, the nature of access between the related Applications and Data Sources is governed only by the Access Conditions in the File Protect rules.
Scope |
Access Conditions |
Controls |
|
Access Conditions can be further granulated by using the Read, Write, and Delete privileges. |
|
File Protect alerts
Alerts for File Protect rule violations are reported in the File Protect Alert category on the Alerts pages. Rule violations are detected when the conditions of access are not met in the scopes set for the rules. File Protect alerts can also be filtered by the specific reason for the alerts (Alert Reason filter).
When to use File Protect
Some of the cases where you can use File Protect are:
Allow read-only or only read and write access to applications to access its log files. For example, disable purging logs from an application's UI.
Exclusively allow files of some extensions to be opened using a featured application—for example, Google Chrome browser to open the HTML pages.
Allow read-only access to a sensitive directory.
Add File Protect rules
All File Protect rules are saved to one File Protect rule stack.
The following steps assume that you are adding File Protect rules to an existing policy. If you are creating a new policy, you must create a policy and add the rules.
|
Multiple Applications and Data Sources in a rule
For a rule with multiple Applications and/or multiple Data Sources, the Access Condition applies to all accessor Applications and to access all the Data Sources. For example, if you allow exclusive read-and-write access to Three apps, App1.exe, App2.exe, and App3.exe, to log files Log1.txt and Log2.txt, only App1.exe, App2.exe, and App3.exe can read and write to the log files.
Rule violations on hosts
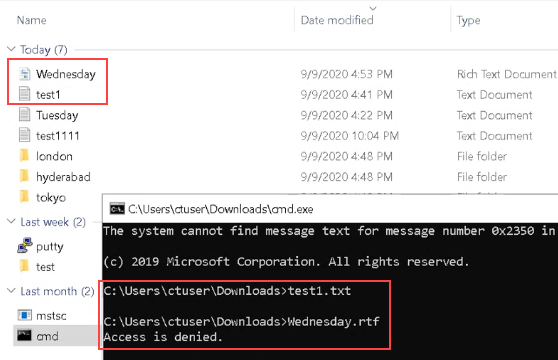
When File Protect rules are violated (Access Conditions are not met), you will see an 'Access is denied' or an equivalent message on the hosts. Currently, alerts are not generated when File Protect rules are violated. |
Edit or move File Protect rules
File Protect rules can be edited or moved across stacks of the policy for better organization. When rules are edited or deleted, you must push the policy to the hosts.
For a more focused view of rules, filter the rules by their attributes. Click the Filters icon, select the rule attributes and click Apply. Ruleattributes include Access Condition, Status (Active and Paused), and Rule Behavior (Monitor mode, Enforce mode, and Log alerts).
To push a policy after the rules are changed, click the Push Policy icon and push the policy to the hosts.
Disable File Protect rules
File Protect rules can be disabled selectively (at the rule level) or at a policy level.
To disable all File Protect rules in a policy, go to Policy Settings, pause File Protect, click Save, and push the policy to the hosts.
To disable File Protect rules selectively, you must locate the rules in your policy and Pause them. Save the policy and push it to the hosts.
Click the 3-dot menu of the policy, click View and Edit Policy, go to the File Protect tab, and set the Status of the rules to Paused.
Next steps
Change AutoTrust settings - AutoTrust can help you regulate application and process behavior for applications and processes that are not yet part of the rules in the policy. AutoTrust settings are set by the level of risk associated with the applications and processes. See AutoTrust settings for policies for more details.
Push the policy - all the changes you make to the File Protect rule stacks, rules, and Policy settings, require that you push the policy again to the hosts for the changes to take effect.
Active policies that are edited and not yet pushed display an Orange exclamation in the Status column on the Policies page. See Push policies to hosts for more details.
Verify File Protect changes - Audit logs are generated when you add or delete File Protect stacks and rules. Go to the Audit Logs page and filter the page by the relevant Audit Actions. See Audit logs for more details.