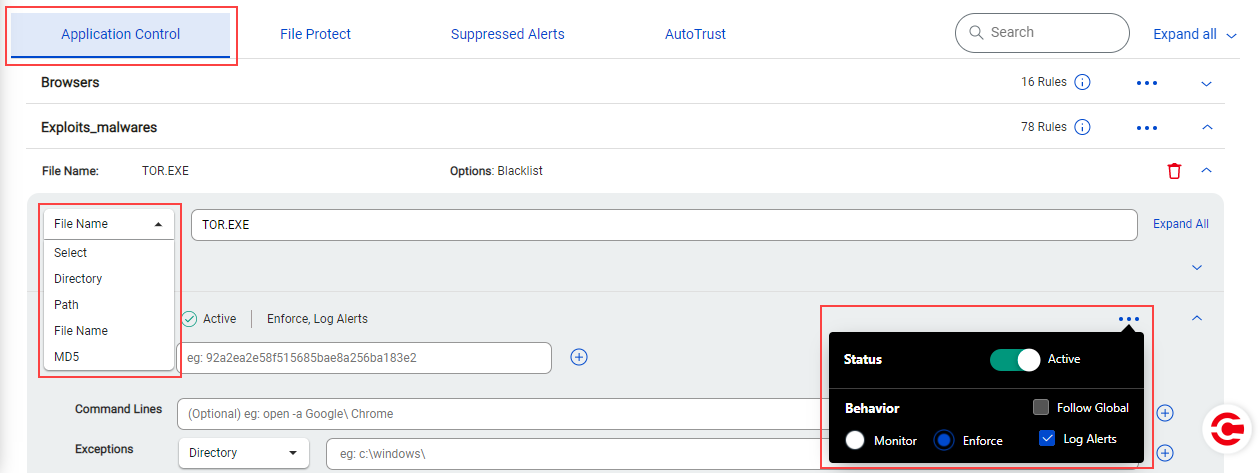
Add Blacklist (Application Control) rules
Blacklist rules define the list of applications and the processes that are 'not' allowed to run/spawn on a host. Blacklisted applications and processes are the undesired and harmful (or unknown) applications and processes; running these on the host can compromise the host and user activities on the host. You can set the Blacklist rules to run in Monitor mode (Blacklisted applications and processes are allowed to run, but violations are reported) or the Enforce mode (Blacklisted applications and processes are blocked/killed/not allowed to spawn).
Scope and controls
See the following table for the scope at which the Blacklist rules can be defined and the controls for the rules.
Scope |
Controls |
|
|
Blacklist alerts
Alerts for Blacklist rule violations are reported in the Blacklist Alert category on the Alerts pages. Rule violations are detected when processes are run at the Blacklisted scopes set for the rules. Blacklist alerts can also be filtered by the specific reasons for the alerts (Alert Reason filter).
Before you begin
In an Xprotect policy (applies to both Host policy and User policy), Blacklist rules can co-exist with Whitelist, Rule Rings, and File Protect rules. For a policy containing multiple types of rules, the overall behavior of the policy depends on Xprotect's intelligent 'order of processing for multiple types of rules in a policy'.
For example, if you enforce a Blacklist rule at a scope that includes an enforced Whitelist rule at a lower scope, all the applications and processes in the Blacklist rule's scope are blocked/killed (including the previously Whitelisted application or process).
Add Blacklist rules
When you enforce Blacklist rules, the applications and processes in the scope are blocked/killed. Enforcing Blacklist rules for top-level or lower-level scopes that are part of Whitelist rules supersedes the Whitelist rules. So, ensure that you consider the impact of the Blacklist rules before you make them Active and enforce them.
The following steps assume that you are adding Blacklist rules to an existing policy. Other cases to add Blacklist rules are when you create a standalone Blacklist policy or when you are creating a new policy and adding Blacklist rules.
|
Multiple MD5s and command lines in a rule
-
Add multiple MD5s to Blacklist multiple MD5s of an application or Blacklist MD5s of multiple applications located in a directory.
-
Add multiple command lines to Blacklist commands run from an application or multiple applications located in a directory.
Rule violations
|
With Blacklist rules enforced on a host, if Blacklisted applications and processes try to run, you will see a 'access denied', 'insufficient privileges' or an equivalent message on the host. : |
Edit or move Blacklist rules
Blacklist rules can be edited or moved across stacks of the policy for better organization. When rules are edited or deleted, you must push the policy to the hosts.
-
For a more focused view of rules, filter the rules by their attributes. Click the Filters icon, select the rule attributes and click Apply. Rule attributes include Rule Type, Status (Active and Paused), and Rule Behavior (Use Policy settings control, Monitor mode, and Enforce mode).
-
To push a policy after the rules are changed, click the Push Policy icon and push the policy to the hosts.
-
To delete rules across the current policy and other policies in which the exact rule exists, click the 3-dot menu of the rule and click Delete Rule or Delete from Policies. When rules are deleted from multiple selected policies, click Immediately Push Policy Update to remove the rule for all relevant hosts.
Disable Blacklist rules
Blacklist rules can be disabled selectively (at the rule level) or at the policy level.
-
To disable all Blacklist rules in a policy, go to Policy Settings, pause Blacklist, click Save, and push the policy to the hosts.
-
To disable Blacklist rules selectively, you must locate the rules in your policy and Pause them. Save the policy and push it to the hosts.
Click the 3-dot menu of the policy, click View and Edit Policy, go to the rule, and set the Status of the rule to Paused.
Next steps
-
Change AutoTrust settings - AutoTrust can help you regulate application and process behavior for applications and processes that are not yet part of the rules in the policy. AutoTrust settings are set by the level of risk associated with the applications and processes. See AutoTrust settings for policies for more details.
-
Push the policy - all the changes you make to the Blacklist rules and Policy settings require that you push the policy again to the hosts for the changes to take effect.
Active policies that are edited and not yet pushed display an Orange exclamation in the Status column on the Policies page. See Push policies to hosts for more details.
-
Verify Blacklist changes - Audit logs are generated when you add or delete Blacklist rules. Go to the Audit Logs page and filter the page by the relevant Audit Actions. See Audit logs for more details.