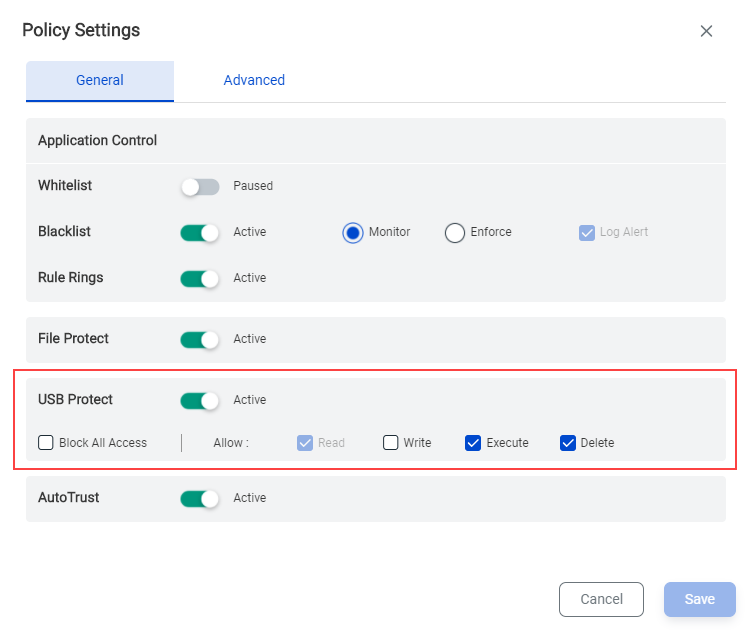
Enable USB Protect for policies
The USB Protect feature in Xprotect is an additional layer of security for hosts that have already been enforced with Application Control and/or File Protect policies. The USB Protect feature is available as an additional Policy setting (on the Policies > Policy Settings > General page) for the Host policy you enforced on a host of hosts.
USB Protect for a Host policy can be set to block all access to USB devices through the USB ports on the hosts or to selectively allow Read, and Write, Execute, or Delete access to USB devices.
USB Protect can be enforced on hosts of all Xprotect-supported Windows and Linux OSes. See Supported OSes for the list of Xprotect-supported OSes.
USB Protect Controls
You can use the following controls to control USB access on the group of hosts (policy) for which you enable the USB Protect feature.
-
Block All Access - block all types of access to USB devices.
-
Read - the host reads the USB device and displays the files saved on the device. You can open the files, but you cannot copy them to the host. Also, you cannot copy files to the USB device.
-
Write - in addition to Read access, you can copy files from or to the USB device.
-
Execute - in addition to Read access, you can execute programs and utilities saved on the USB device.
-
Delete - in addition to Read access, you can delete the files on the USB device.
The actual time when the USB Protect is enforced or disabled on the hosts depends on when the last operation was performed on the hosts, and the duration you specify for the Agent Fetches Command Every option (on the Policies > Policy Settings > Advanced page) for the policy on the host.
Expected behavior
The USB Protect feature in Xprotect is designed to regulate access to USB devices connected through the Mass Storage Class (MSC) or Picture Transfer Protocol (PTP) connection modes/protocols. USB Protect does not prevent access to devices connected to hosts by using the Media Transfer Protocol (MTP) or similar protocols. So, you will see that mobile phones connected to hosts can transfer data to and from the hosts and execute utilities on the hosts without any restrictions.
When to use USB Protect
Enable USB Protect for a policy and consequently the hosts that use the policy when you want to:
-
Completely lock down USB access to mission-critical and supporting workloads, Point of Sale (PoS) systems, and end user hosts. For example, use Block All Access.
-
Enforce restricted access to USB devices on hosts that must occasionally use USB devices. For example, enable only Execute permissions to allow running utilities on hosts, or only Read permissions to allow users to open documents and media files.
-
Enable data backup activities from on to hosts by using only Write permissions.
-
Enable USB device cleanup activities by enforcing only Delete permissions.
Enable USB Protect
When you enable USB Protect for a policy, all the hosts on which the policy is enforced using the USB Protect settings.
The actual time when the USB Protect feature is enforced or disabled on the hosts depends on when the last operation was performed on the hosts, and the duration you specify for the Agent Fetches Command Every option (on the Policies > Policy Settings > Advanced page).
|
Alternatively, you can enable USB Protect for a policy when you create and push the policy to a group of hosts.
Alerts
Currently, alerts are not generated when USB devices violate the USB Protect settings on a host.
Disable USB Protect
Disable USB Protect policies when you want to allow unrestricted access to USB devices to a group of hosts. Remember that all hosts in the group will have unrestricted access to USB devices.
-
To disable the USB Protect feature, go to the General Policy settings of the policy (on the Policies page) and set USB Protect to Paused (turns Grey).
Verify USB Protect status
Currently, Audit logs are not generated when you enforce or disable USB Protect. You must verify the status of this feature directly on the hosts. For example, if you set USB Protect to Read-only access to USB devices, users must not be able to execute utilities from USB devices.